
I talked about MicroVMs in my previous article. In this article, we will examine Firecracker in detail. Firecracker is developed by AWS and it is used in Fargate, which is a serverless compute for containers solution and it is used in lambda which it offers as a function as a service solution. If you’re curious about Firecracker, let’s get started!
What is Firecracker
Firecracker is a virtualization technology for running the workloads on MicroVMs. As I mentioned in a previous article, MicroVMs are a technology that combines some of the advantages of traditional VMs and containers. At the beginning of these advantages are the resource efficiency and isolation of VMs and the quick start-up times of containers.
Going into more detail, Firecracker was written based on CrossVM, a Virtual Machine Monitor written in Rust. (CrossVM is a tool to run Linux applications inside ChromeOS)
The purpose of developing Firecracker is explained as follows: When Lambda was first released, different ec2 machines were created for each user, thus providing strong isolation and security. To make this more efficient, the AWS team started developing this project. The reason for not using other alternatives here may be security related issues. Thanks to Rust, they took a step forward with security. As I said at the beginning of the article, Firecracker is currently used in AWS Lambda and Fargate. In addition, it can be used with many technologies, for example, it is possible to run containers thanks to firecracker-containerd.
Let’s Go Deeper!
In this section of the article, I utilized information from the project’s own documentation. You can find many details, especially in the design document. First and foremost, let’s take a look at the overall structure of Firecracker and the components it comprises.
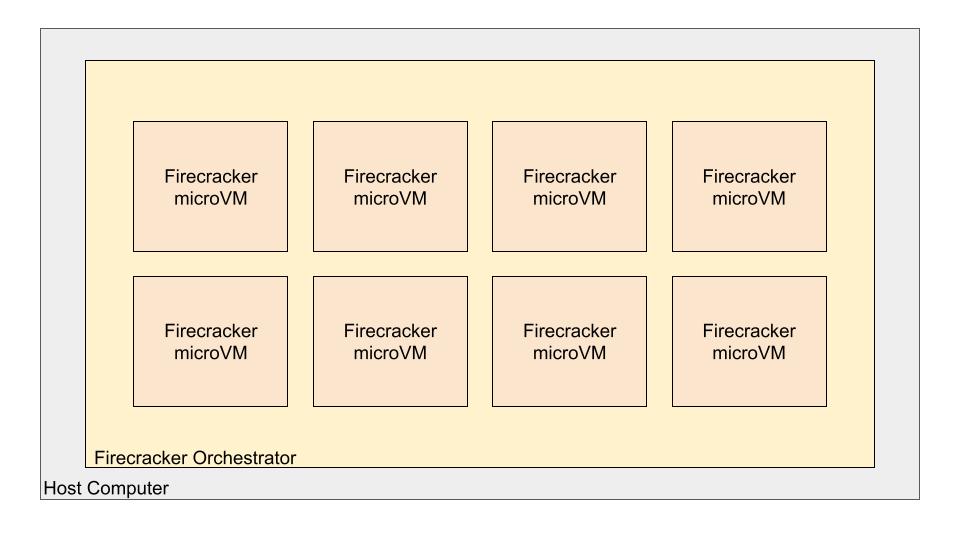
Firecracker, just like its predecessor CrossVM, requires KVM (Kernel-based Virtual Machine). It is an alternative to QEMU. It can even be considered as an alternative to the QEMU and libvirt stack. As you can see in the image above, an orchestrator manages multiple microVMs. Each microVM operates independently from one another.
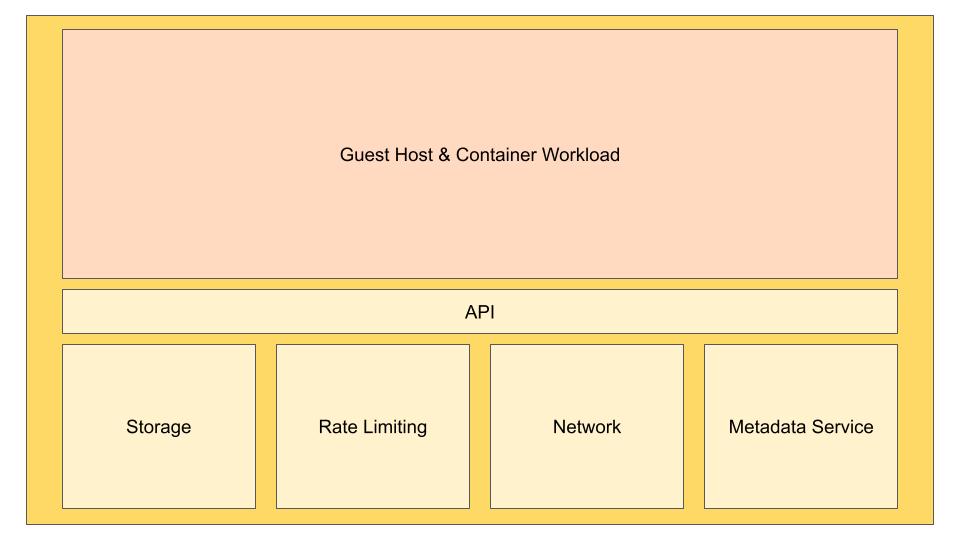
Each microVM has its own kernel, but this is a very minimal kernel. It contains very few components, thus creating a lightweight environment. Not every Linux distribution can be used as a guest host because it is a special kernel.
Each firecracker microVM has its own unique process so, microVMs don’t share memory with any other microVM. Each microVM has threads responsible for API, VMM and vCPU. Let’s examine these threads now!
API Thread
This thread exists for communication with the firecracker microVM. Many things can be managed through the API. For example:
instanceStart: Powers on the microVM and starts the guest OS
flushmetrics: Flushes the metrics
SendCtrlAltDel: Send the CTRL+ALT+DEL key sequence to guest host (intel and amd)
VVM
Firstly, VMM thread responsible for the machine model and minimal legacy device model. Machine model defines characteristics and behaviors of microVM. If minimal legacy device model, defines legacy devices in the microVM
MicroVM metadata service (MMDS): It holds certain configuration and data of MicroVM, this data can be presented to the user via API. Also metadata maintained through api is fully configured by users
VirtIO Net, VirtIO Block emulated devices: these devices provide storage and network access.
I/O rate limiting: There is a rate limiter to limit the operations performed by microVMs running on the host computer. This rate limiting uses a token bucket algorithm with 2 buckets. one bucket is used to limit the bandwith and the other bucket is used to limit the number of operations per second. Users can configure rate limiting via API. In this way, the user can create rate limiting flexibly.
One or more vCPU threads (one per guest CPU core): in this part, the customer workload runs
Security
AWS team mentions that it offers an isolated environment. For this, the first suggestion is to run it with a jailer. If you are going to use the firecracker in a production environment, the jailer has an important place here. In the scenario where you are working with a jailer, the firecracker process is run by the jailer and some restrictions are made. Thus, the security risk is reduced. In addition, seccomp filters are used to limit host system calls so unwanted system calls can be pretended. Thanks to Cgroups and Quotas, a fair resource distribution between microVMs is ensured by limiting CPU and bandwidth and isolation is ensured.
Monitoring
In Lambda logs, we can observe metrics such as the duration of Lambda execution and the amount of memory it consumes. Similarly, Firecracker data and metrics are also tracked through logs. logs and metrics are emited on a named pipe. The logs are flushed every 60 seconds after it starts running or in the event of a panic. Additionally, the same operation can also be performed with flushmetrics on the API.
To Sum Up
This project is well suited for AWS Lambda in my opinion. Because millions of users and millions of functions are running. It is very important to manage the load in an efficient way here, and at the same time, it is important to establish a secure and isolated structure. Here, we can see the benefit of being written with rust. If you are going to make a multi-tenant application, I think firecracker is an option that should definitely be considered. It is also a great advantage that both CrossVM and Firecracker are open source. Thanks to both Google and the AWS team for supporting open source!
References
- Red Hat Blog. “All You Need to Know About KVM Userspace.” Red Hat, https://www.redhat.com/en/blog/all-you-need-know-about-kvm-userspace.
- Firecracker GitHub Repository. “Design Document” Firecracker, https://github.com/firecracker-microvm/firecracker/blob/main/docs/design.md.
- CrossVM Github Repository, https://github.com/google/crosvm
- Firecracker-Containerd Github Repository, https://github.com/firecracker-microvm/firecracker-containerdhttps://github.com/firecracker-microvm/firecracker-containerd
- Geeksforgeeks, “Difference between Process and Thread”, https://www.geeksforgeeks.org/difference-between-process-and-thread/https://www.geeksforgeeks.org/difference-between-process-and-thread/

Leave a Reply